Strategic Protection: Releasing the Power of Corporate Security Steps
Wiki Article
Reliable Security Services to Guard Your Corporate Properties
In today's quickly progressing service landscape, protecting company possessions has ended up being a lot more critical than ever before. Trustworthy safety solutions are necessary to guarding useful resources, sensitive info, and the overall well-being of an organization. With a boosting number of digital and physical threats, organizations require thorough protection remedies that guarantee their properties stay safeguarded at all times.Our expert safety solutions supply a range of advanced services customized to meet the distinct demands of your business environment. From physical protection actions such as accessibility control systems and monitoring solutions to digital danger discovery and emergency reaction methods, we supply a holistic method to guarding your possessions.
Our dedicated group of protection specialists is committed to delivering reliable and dependable security remedies that mitigate danger and enhance the overall safety and security of your company. With our solutions, you can have assurance recognizing that your company properties remain in capable hands.
Physical Protection Solutions
- Physical safety and security options are essential for protecting business possessions and ensuring the safety of workers and delicate info. These options encompass a series of steps and innovations created to stop unauthorized accessibility, theft, criminal damage, and various other hazards to physical rooms.
One of the main elements of physical security is access control systems (corporate security). These systems allow just authorized individuals to get in limited areas, utilizing approaches such as essential cards, biometric scans, or PIN codes. By limiting accessibility to sensitive locations, companies can minimize the risk of burglary, sabotage, or unauthorized disclosure of personal info
Another vital facet of physical security is surveillance. Closed-circuit television (CCTV) cams are typically deployed throughout a center to keep an eye on activities and discourage potential trespassers. With innovations in technology, video analytics and facial recognition abilities can boost the efficiency of surveillance systems, allowing real-time threat discovery and action.
Physical barriers, such as fences, gates, and reinforced doors, also play a crucial duty in shielding company properties. These obstacles function as deterrents and make it much more difficult for unauthorized individuals to get. Additionally, security system and activity sensors can inform safety personnel or police in the event of a violation or questionable task.
Digital Risk Detection
Digital Danger Detection is a vital aspect of detailed security actions, making use of sophisticated modern technologies to recognize and reduce possible cyber threats to company possessions. In today's electronic landscape, services face an increasing variety of advanced cyber attacks that can cause substantial economic losses and reputational damages. Digital Risk Detection intends to proactively recognize and react to these hazards before they can trigger injury.To successfully discover electronic threats, companies use a variety of innovative technologies and strategies. These include invasion detection systems, which monitor network website traffic for suspicious task, and malware analysis devices, which analyze and identify malicious software program. Additionally, behavioral analytics and artificial intelligence formulas are utilized to spot abnormalities in individual habits and recognize prospective expert dangers.
Digital Risk Discovery likewise entails real-time tracking of network facilities and endpoints to respond and determine to energetic hazards. Protection operations facilities (SOCs) play a vital role in this process, as they continuously examine and check safety alerts to swiftly detect and react to possible risks. Risk knowledge feeds are utilized to stay updated on the latest cyber risks and susceptabilities.
Monitoring and Monitoring Providers
To make certain thorough protection measures, organizations can use monitoring and monitoring services as a necessary component of protecting their company assets. Surveillance and surveillance solutions provide real-time surveillance and analysis of activities within and around the company, allowing timely recognition and action to potential safety and security risks.By using sophisticated monitoring technologies such as CCTV electronic cameras, activity sensing units, and accessibility control systems, companies can effectively monitor their facilities and identify any kind of unapproved access or questionable tasks. This positive method acts as a deterrent to prospective criminals and helps preserve a secure atmosphere for workers, site visitors, and beneficial properties.
Along with physical security, companies can likewise gain from electronic tracking services. These solutions involve the surveillance of digital networks, systems, and devices to determine any kind of malicious or uncommon activities that might compromise the safety and security of business information and delicate info. With continual surveillance and analysis of network website traffic and system logs, prospective protection breaches can be found early, permitting for prompt therapeutic action.
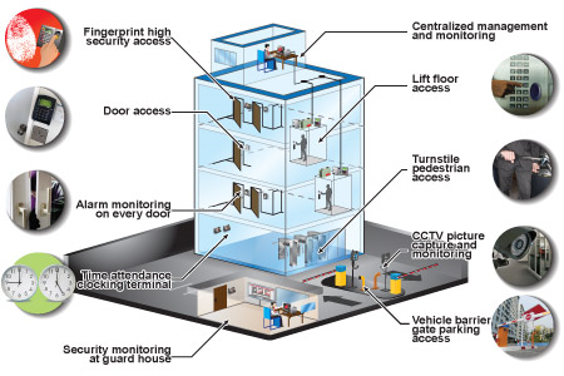
Gain Access To Control Equipment

These systems make use of different innovations such as vital cards, biometric scanners, and PIN codes to reject or approve accessibility to people. By applying access control systems, firms can efficiently take care of and limit access to important locations, decreasing the threat of unauthorized access and possible burglary or damages to valuable see properties.
Among the vital advantages of gain access to control systems is the ability to track and keep track of the motion of people within a facility. This feature enables companies to produce comprehensive reports on who accessed particular areas and at what time, providing important data for security audits and examinations.
Additionally, access control systems can be integrated with other protection actions, such as monitoring cameras and security system, to enhance general security. In case of a safety and security breach or unauthorized gain access to attempt, these systems can set off prompt alerts, making it possible for quick reaction and resolution.
Emergency Action and Event Administration
In the realm of thorough security procedures, the emphasis now changes to the essential aspect of successfully handling emergency situation response and occurrence administration in order to guard company possessions. Prompt and reliable response to cases and emergencies is crucial for minimizing possible losses and protecting the well-being of staff members and stakeholders.Emergency situation reaction and case administration involve a methodical method to managing unpredicted occasions and interruptions. This includes creating robust plans and methods, training employees, and collaborating with relevant authorities. By developing clear lines of interaction and assigned emergency response groups, companies can make sure a swift and collaborated response when faced with emergency situations such as fires, all-natural calamities, or security breaches.
Incident management goes past instant emergencies and incorporates the monitoring of any kind of unintended events that may disrupt normal business procedures. This can consist of occasions such as power interruptions, IT system failures, or supply chain disruptions. Reliable occurrence administration includes quickly examining the situation, applying necessary measures to minimize the influence, and recovering regular procedures as swiftly as feasible.
Conclusion
To conclude, dependable safety services play an important duty in guarding company properties. By carrying out physical protection solutions, digital risk detection, tracking and monitoring solutions, access control systems, and emergency reaction and incident administration, companies can mitigate risks and safeguard their important resources. These solutions supply a robust protection versus possible risks, guaranteeing the safety and security and integrity of corporate assets.One of the key elements of physical security is accessibility control systems.Digital Threat Detection is an important aspect of extensive safety actions, using advanced technologies to determine and mitigate prospective cyber threats to corporate possessions. Safety operations facilities (SOCs) play a critical duty in this process, as they continually assess and keep an eye on safety and security signals to rapidly spot and react to prospective hazards.Continuing the conversation on extensive safety actions, gain access to control systems play a vital check over here role in making certain the securing of company properties. By executing physical protection options, digital danger tracking, detection and security solutions, gain access to control systems, and emergency situation reaction and occurrence management, organizations can reduce dangers and safeguard their valuable sources.
Report this wiki page